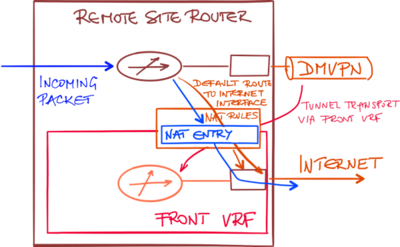
The outer encapsulated packet belongs to one vrf domain called the front door vrf fvrf while the inner protected ip packet belongs to another domain called the inside vrf ivrf.
Front door vrf nat.
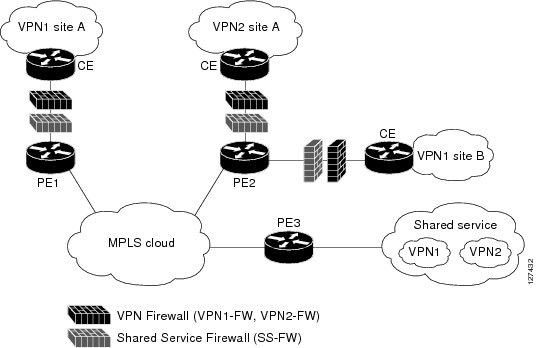
Ipsec and nat across bgp internet routers.
Stated another way the local endpoint of the ipsec tunnel belongs to the fvrf while the source and destination addresses of the inside packet belong to the ivrf.
By using front door vrf we are isolating transport network usually internet facing and this allows us to configure default route that won t interfere with routing in our global table.
Crypto keyring dmvpn vrf internet pre shared key address 0 0 0 0 0 0 0 0 key pass.
Ospf in our case.
There must be an entry in the global routing table for example a default route that will send the incoming packet toward the internet facing interface.
Ip vrf vrf01 rd 100 1 route target export 100 1 route target import 100 1.
Interface fastethernet0 0 description global table interface ip address 172 16 1 200 255 255 255 0 no ip proxy arp ip nat outside ip virtual reassembly.
Nat rules configured between global routing table and front vrf configuring the nat rules between the global routing table and transport vrf is not enough.
Default leak from front door vrf to grt nat overload.
If this ip fits into the same subnet as configured on your outside nat interface ip address 209 133 x b 255 255 255 224 so the ip of 209 133 x y looks as directly connected there is a problem with the fact that this interface being in vrf the router in most cases will not respond to arp requests for aliases directly connected ip s for.
00 05 00 ip nat inside source list acl nat out int gi6 vrf internet a overload ip access list extended acl nat out 10 permit ip any any int gi6 ip vrf forwarding internet a ip address 12 45 78 89 30 ip nat outside int gi1 ip address 172 16 0 22 30 ip nat inside ping 12 45 78 90 this.
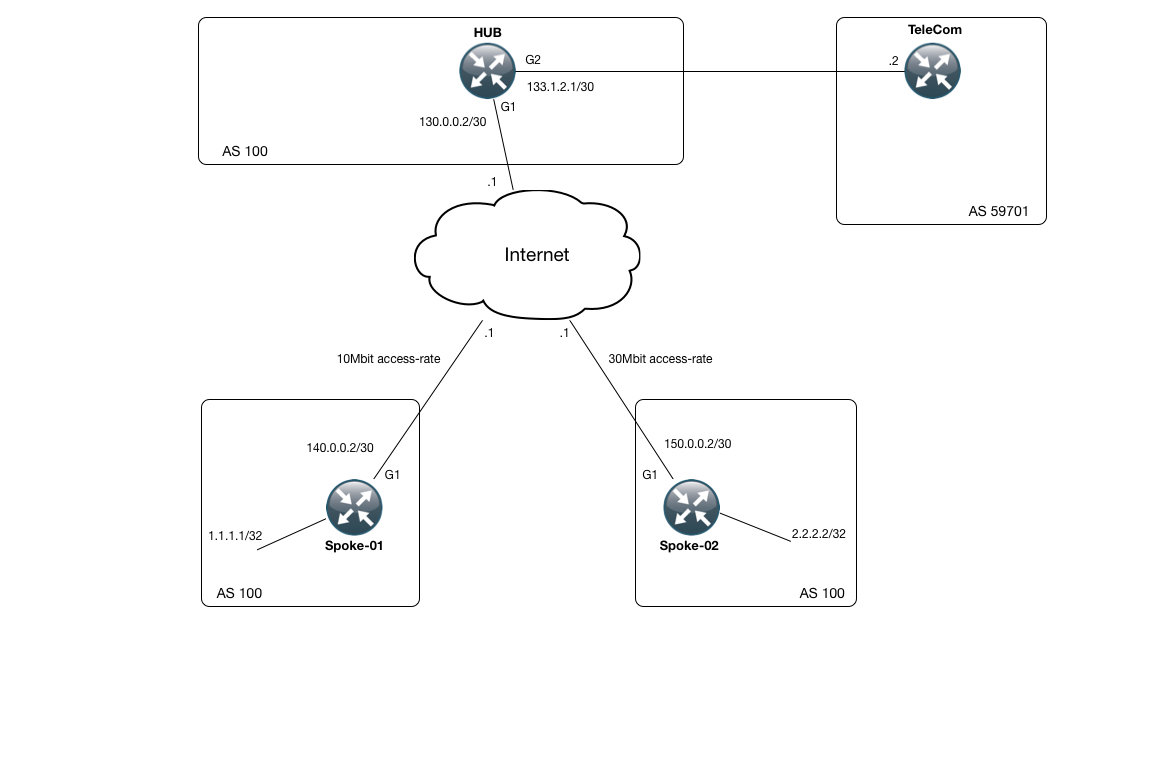
In order to understand the use of front door vrfs let us use a simple topology as below where we will create a simple gre tunnel between r1 and r4.
As you can see we did not move the tunnel11 interface from the global routing table to the routing table for vrf pipe.
David bombal 1 488 views.
Both r1 and r4 will learn about the tunnel destination address via underlying protocol i e.
All we did is stitch them together.
Vrf aware vpn using front door vrf fvrf ivrf duration.
Khawar butt 7 999 views.
Modify the tunnel interface to stitch the tunnel to the front door vrf.
Answers part 1 duration.
When internet interface and tunnel interface are in the same vrf on the hub everything works well.
I d like to configure dmvpn hub behind static nat.
Interface fastethernet1 0 ip vrf forwarding vrf01 ip address 192 0 2 1 255 255 255 0.